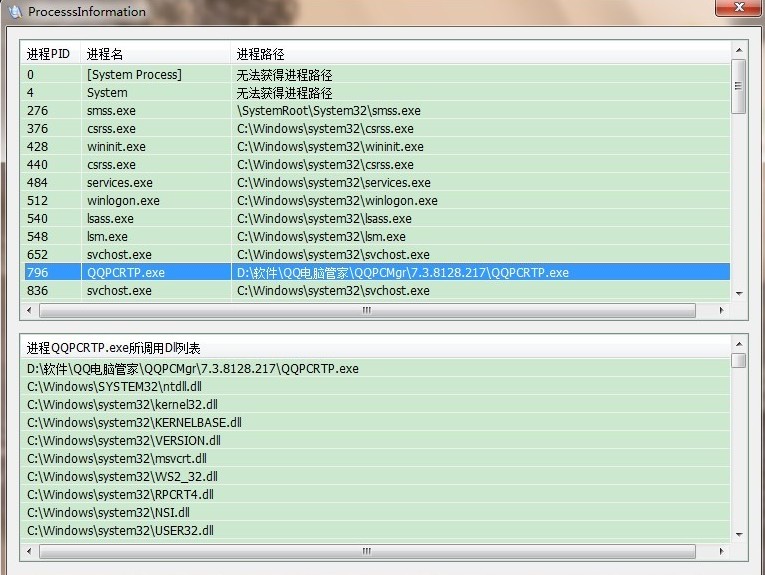
// -----------------------// FileName:
// ProcessInfo.h
// remarks:
//& have spent Based on the implementation of the application layer, some processes, such as killing the soft process, etc., can not get the call DLL list.
// -----------------------
#pragma once
#include <vector>
struct ProInfo
{
//Save process PID
unsigned int uPID;
//Save process name
CString strPrceName;
//Save process path
CString strFullPath;
//Save the process call DLL name and path
std::vector<CString> strDLLNameArr;
};
class CProcessInfo
{
private:
//This is for the claim
BOOL EnableDebugPrivilege (BOOL fEnable);
public:
//Save process name
std::vector<ProInfo> strPrceInfoArr;
CProcessInfo();
~CProcessInfo();
//Get the process name
void GetProcessName (void);
};
// ------------------------------------------------------------------------------------------------------------------------
// FileName:
// ProcessInfo.cpp
// remarks:
//& have spent & have spent & have spent & have spent & have spent Based on the implementation of the application layer, some processes, such as killing the soft process, etc., can not get the call DLL list.
// ------------------------------------------------------------------------------------------------------------------------
#include "stdafx.h"
#include "ProcessInfo.h"
#include "TlHelp32.h"
#include "StrSafe.h"
#include "Psapi.h"
//Prevent error LNK2019
#pragma comment(lib, "psapi.lib")
CProcessInfo::CProcessInfo()
{
}
CProcessInfo::~CProcessInfo()
{
}
BOOL CProcessInfo::EnableDebugPrivilege(BOOL fEnable)
{
BOOL fOk = FALSE;
HANDLE hToken;
//Gets the access token for the process
if (OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES,&hToken))
{
TOKEN_PRIVILEGES tp;
tp.PrivilegeCount = 1;
//View system privilege values and return a LUID structure
LookupPrivilegeValue(NULL, SE_DEBUG_NAME, &tp.Privileges[0].Luid);
tp.Privileges[0].Attributes = fEnable ? SE_PRIVILEGE_ENABLED : 0;
//Enable/close privileges
AdjustTokenPrivileges(hToken, FALSE, &tp, sizeof(tp), NULL, NULL);
fOk = (GetLastError() == ERROR_SUCCESS);
CloseHandle(hToken);
}
else
{
return 0;
}
return(fOk);
}
void CProcessInfo::GetProcessName (void)
{
HANDLE hProcessSnap = NULL;
HANDLE hProcessDll = NULL;
BOOL bRet = FALSE;
//Initialize dwSize to 0 or Process32First fails
PROCESSENTRY32 pe32 = {0};
MODULEENTRY32 me32;
LPVOID lpMsgBuf;
LPVOID lpDisplayBuf;
DWORD dwError;
ProInfo proinfo;
LPCTSTR pszFormat = TEXT(" An error was encountered while starting the service ! %s");
//Create a process snapshot
if(!EnableDebugPrivilege(1))
{
MessageBox(NULL, _T(" Submission failed! "), _T(" prompt "), MB_OK|MB_ICONEXCLAMATION);
}
hProcessSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (hProcessSnap == INVALID_HANDLE_VALUE)
{
dwError = GetLastError();
FormatMessage(
FORMAT_MESSAGE_ALLOCATE_BUFFER|
FORMAT_MESSAGE_FROM_SYSTEM|
FORMAT_MESSAGE_IGNORE_INSERTS,
NULL,
dwError,
MAKELANGID(LANG_NEUTRAL, SUBLANG_DEFAULT),
LPTSTR(&lpMsgBuf),
0,
NULL);
lpDisplayBuf = (LPVOID)LocalAlloc(
LMEM_ZEROINIT,
(lstrlen((LPCTSTR)lpMsgBuf)+lstrlen(pszFormat))*sizeof(TCHAR));
//Formatted string
StringCchPrintf(
(LPTSTR)lpDisplayBuf,
LocalSize(lpDisplayBuf), //The number of bytes
pszFormat,
lpMsgBuf);
CString strTemp;
strTemp.Format(TEXT(" Error code: :%d"), dwError);
::MessageBox(NULL, (LPCTSTR)lpDisplayBuf, strTemp, MB_OK|MB_ICONEXCLAMATION);
//Clean up the allocated memory
LocalFree(lpMsgBuf);
LocalFree(lpDisplayBuf);
return;
}
pe32.dwSize = sizeof(PROCESSENTRY32);
Module32First(hProcessSnap, &me32);
if (Process32First(hProcessSnap, &pe32))
{
do
{
WCHAR path[MAX_PATH]={0};
proinfo.uPID = pe32.th32ProcessID;
proinfo.strPrceName = pe32.szExeFile;
HMODULE hModule;
HANDLE hProcess;
DWORD needed;
hProcess=OpenProcess(PROCESS_QUERY_INFORMATION | PROCESS_VM_READ, false, pe32.th32ProcessID);
if (hProcess)
{
//The enumeration process
EnumProcessModules(hProcess, &hModule, sizeof(hModule), &needed);
//Gets the full path of the process
GetModuleFileNameEx(hProcess, hModule, path, sizeof(path));
//Save the path
proinfo.strFullPath = path;
}
else
{
proinfo.strFullPath = _T(" Unable to obtain process path ");
}
strPrceInfoArr.push_back(proinfo);
}
while (Process32Next(hProcessSnap, &pe32));
}
std::vector<ProInfo>::iterator iter;
for (iter = strPrceInfoArr.begin(); iter != strPrceInfoArr.end(); iter++)
{
//Take a snapshot of the process
hProcessDll = CreateToolhelp32Snapshot( TH32CS_SNAPMODULE, iter->uPID);
me32.dwSize = sizeof(MODULEENTRY32);
if (!Module32First(hProcessDll, &me32 ) || iter->uPID==0)
{
continue;
}
do
{
iter->strDLLNameArr.push_back(me32.szExePath);
}
while( Module32Next(hProcessDll, &me32));
}
//Close the privilege
EnableDebugPrivilege(0);
//Close the kernel object
CloseHandle(hProcessSnap );
}
